Ransomware, it’s everywhere. We had hoped that the notorious file-encrypting ransomware called CryptoLocker was defeated after law enforcement knocked out its infrastructure last year, but CryptoLocker and its close cousin CryptoWall have come back stronger than ever.
Ransomware is malware that prevents you from using your files or your computer, and then extorts money from you in exchange for a promise to unlock them.
We’d like to show you more about the newest kinds of ransomware, how they work, and what you as an organization or individual can do to stay safe.
Ransomware: a brief history
Ransomware and fake-antivirus have been around for many years, relying on social engineering to trick computer users into paying the cybercriminals, so their phony warnings claim, to avoid fines from police for supposed crimes, or to clean up “viruses” on their computers that don’t actually exist.
But CryptoLocker and CryptoWall – variations of the malware we sometimes call crypto-ransomware or cryptoware – don’t bother with that sort of trickery. The attackers tell victims up-front that their files have been encrypted by the crooks. Unless you pay for the encryption key held by the attackers, the crooks destroy the private encryption key, making it impossible to recover your files.
How it works
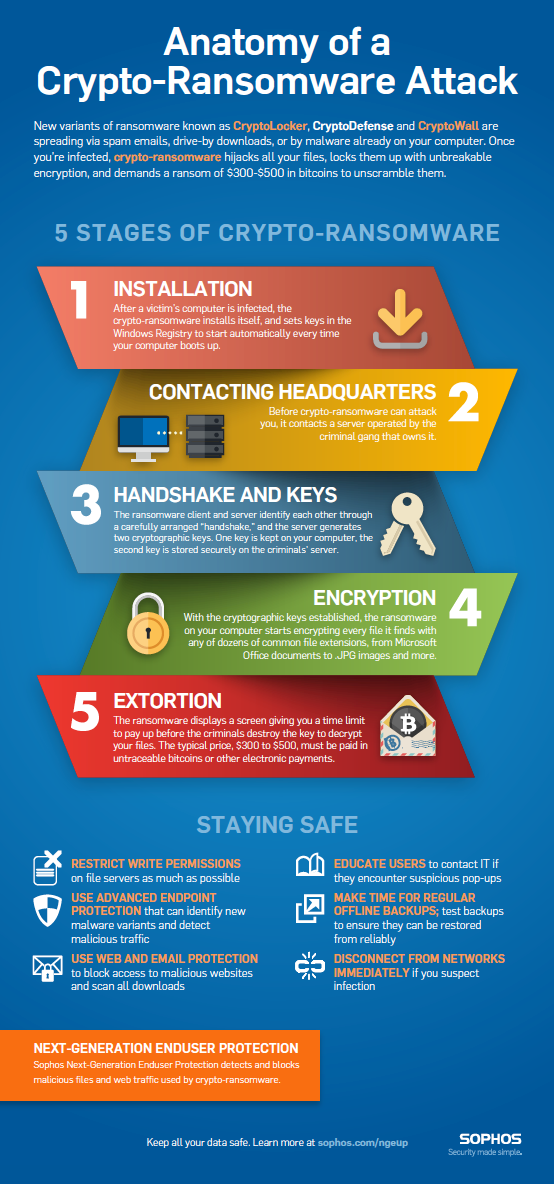
A ransomware attack goes through five stages from the time it installs on your computer to the appearance of the ransom warning on your screen. You can download our step-by-step infographic to learn about the stages of an attack, and get tips on staying safe.
Ransomware protection, prevention and mitigation
If you suspect you’ve been compromised by ransomware, you can remove the malware using our Free Virus Removal Tool. Sadly, there’s not much you can do to get your files back except to pay the ransom – the encryption is too strong to crack.
We don’t think paying the ransom is the best idea because there’s no guarantee the criminals won’t up the ante, or that they’ll actually follow through on their promise to send you the keys to decrypt your files. And paying the ransom also supports a cybercriminal enterprise that will ensnare more victims.
But it’s easy to understand why so many people do pay the ransom, especially if you’ve lost invaluable corporate or personal data.
Recently, a sheriff’s office in Tennessee paid a ransom to CryptoWall cybercrooks, and other police departments and public sector organizations have done the same.
Really, the best defense is a proactive one: always back up all your files, and use anti-malware and anti-spam protections.
To learn more about protecting your organization against ransomware attacks, download our free whitepaper, CryptoLocker, CryptoWall and Beyond: Mitigating the Rising Ransomware Threat.
This whitepaper explains:
- A brief history of ransomware, from Winlockers to today’s crypto-ransomware
- How ransomware works and why it is so dangerous
- Specific recommendations that can dramatically reduce your vulnerability
The best ransomware defense: Next-generation protection from Sophos
Before ransomware can do its dirty work, it must contact a live command and control server. Next-generation firewalls such as the Sophos UTM can help block that. So can today’s best client anti-malware software. Our Next-Generation Enduser Protection offers Malicious Traffic Detection (MTD) that goes wherever you go, detecting and stopping malware when it connects to attackers’ servers.
Next-Generation Enduser Protection is the integration of Sophos’s innovative endpoint, mobile and encryption technologies to deliver better protection and simpler management.
To learn more about how to try it for free, visit sophos.com/ngeup.
Net Universe ǀ Connecting Solutions – Why choose Sophos Endpoint Protection? Our innovative technology and threat intelligence
[…] one example, MTD can detect if one of your endpoints is compromised by the ransomware called CryptoWall, which uses a secret encryption key to scramble all your files and connected drives and demands a […]
Why choose Sophos Endpoint Protection? Our innovative technology and threat intelligence — The Cloud Key
[…] one example, MTD can detect if one of your endpoints is compromised by the ransomware called CryptoWall, which uses a secret encryption key to scramble all your files and connected drives and demands a […]
Ransomware | Brubaker Consulting
[…] Make sure you have good backups of your files, Ransomware is rampant these days. http://blogs.sophos.com/2015/03/03/anatomy-of-a-ransomware-attack-cryptolocker-cryptowall-and-how-to… […]
Actus Sécurité Grand public 2015 S10 | La Mare du Gof
[…] => Analyse d’un Ransomware : CryptoLocker . 02/03/2015. «Qu’en est-il des ransomwares cryptographique à l’heure actuelle ? (Cet article est extrait de notre Observatoire de la Cybercriminalité « Analyse d’un Ransomware– CryptoLocker »). Une conférence sur les ransomwares sera donnée très prochainement par les experts Lexsi à Paris, Lyon et Lille (…).» Source : www.lexsi-leblog.fr/cert/analyse-dun-ransomware-cryptolocker.html Billets en relation : 03/03/2015. Anatomy of a ransomware attack: CryptoLocker, CryptoWall, and how to stay safe (Infographic) : blogs.sophos.com/2015/03/03/anatomy-of-a-ransomware-attack-cryptolocker-cryptowall-and-how-to-stay-s… […]
ste williams – TeslaCrypt ransomware attacks gamers
[…] firewalls and anti-malware software that can detect suspicious traffic to the command and control server can stop the malware when it connects to attackers’ […]
RANSOMWARE o Extorsión Digital | Delfín Abzueta
[…] de los ataques de ransomware, para lo cual una reconocida empresa de seguridad desarrolló una muy buena infografía que puede ser consultada y […]
World Backup Day – why backups are so important, and some data protection tips for businesses | Sophos Blog
[…] growing threat of ransomware like CryptoLocker and CryptoWall in the past couple of years has underscored the importance of backups, but it’s not only […]
Net Universe ǀ Connecting Solutions – World Backup Day – why backups are so important, and some data protection tips for businesses
[…] growing threat of ransomware like CryptoLocker and CryptoWall in the past couple of years has underscored the importance of backups, but it’s not only […]
World Backup Day – why backups are so important, and some data protection tips for businesses — The Cloud Key
[…] growing threat of ransomware like CryptoLocker and CryptoWall in the past couple of years has underscored the importance of backups, but it’s not only […]
World Backup Day – why backups are so important, and some data protection tips for businesses | Array.ws | All About The Computer's
[…] growing threat of ransomware like CryptoLocker and CryptoWall in the past couple of years has underscored the importance of backups, but it’s not only […]
Kathy
“The best ransomware defense: Next-generation protection from Sophos”
I have a machine sitting 3 feet from me that Cryptowall blew through without a problem. Maybe you could spend less time blogging and more time updating.
Mike
A machine of ours got hit with crypto wall 3.0. we have a backup from a couple weeks ago so there’s only a few files that were recently updated / created since that backup.
Don’t want to pay the $700 (or actually, anything) to the hackers.
Any chance those few files can be decrypted with today’s computers in days or weeks? Would you crack 1, then get the key and apply it to the other files?
How would I begin to do this? Can I do it concurrently on a few machines?
thanks!
Paul Ducklin
Commiserations.
As far as I am aware, the way the encryption works in the more recent versions of CryptoWall means that it’s unlikely you will see those files again without paying. Even if there were a possibility to decrypt in some cases, it’s hard to say whether tools that claim to unscramble your files will work in any specific case.
There are various free tools out there that claim that they may be able to decrypt earlier CryptoWall versions…the question is, how long to spend trying them (and how to tell if they are legitimate, given that many people who go looking for that sort of thing are fairly desperate).
The crooks, of course, are gambling that the $700 will be less than it would cost to get back to where you were by other means, including trying a bunch of free tools or typing in your stuff all over again. Obviously, we have to recommend not doing business with extortionists, but we also accept that sometimes there is too much at stake in the data to tell the crooks to take a hike.
Having said that, if you possibly can, see if you can make do with restoring a clean PC, recovering your backup, cutting your losses, taking it on the chin, and being one of those victims who stuck it to the crooks. (If you do, please come back to this article and take some public pride, albeit anonymously…not much compensation, I admit but we’ll pump the air on your behalf :-)
This article sets out some opinion on whether to pay or not, though it may be cold comfort in your case:
https://nakedsecurity.sophos.com/2015/03/19/ransomware-should-you-pay/
Anonymous
I was also a victim of CryptoLocker. RAR Files have remained intact so you can keep important documents in that way
Mark Stockley
Remember that there are many, many different strains of ransomware and that malware evolves over time. Tricks that work today may not work tomorrow. If you’re rar files were ignored then think yourself lucky but please don’t rely on keeping files in rar archives as a form of defence.